This blog has advocated for the use of two-factor authentication. Recently, however, it was revealed that several high profile social media accounts were hacked, despite using two factor authentication.
What happened?
Update: See Wired’s new piece on the subject: So Hey You Should Stop Using Texts for Two-Factor Authentication
Update: See Joint investigation of Ashley Madison by the Privacy Commissioner of Canada and the Australian Privacy Commissioner at Paragraph 72, arguing that multiple iterations of the same factor is not multi-factor.
Theft
First, it is worth discussing factors themselves. According to David Bisson:
Authentication factors come in three different types: knowledge factors (“something you know”), possession factors (“something you have”), and inherence factors (“something you are”).
One might add time and location as additional types of factors.
Most social media services, for instance, use something you know (a password) and what they presume qualifies as something you have — your cell phone (which receives a text with a code). However, to a determined adversary, a cellphone is not necessarily a device you uniquely possess. Why? Because malefactors can fairly easily gain access to your cell account, replicate phone or use malicious code to intercept texts. Once that is done, the malefactor can intercept your texts, including any text-to-cell-phone codes.
If it is easy to intercept your texts, then a cell phone likely doesn’t count as a true “thing you have” for two-factor authentication purposes. The code merely becomes “something you know,” insecurely delivered to you. And that is insufficient for true two-factor authentication.
Social Engineering
Another attack vector is social engineering.
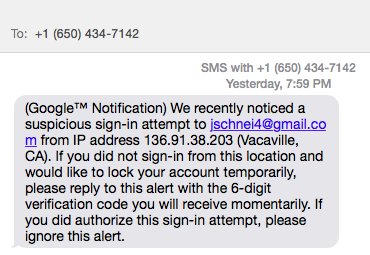
A security researcher, Alex MacCaw, reports a social engineering attack against text-to-cell two-factor authentication. Adversaries are acquiring passwords to social media accounts (the usual way) and then, pretending to be the social network, text the account owner, claiming that the account has been compromised and to please reply with the next code they receive. The attacker then triggers the social network to send a verification code and, when the owner replies, assumes control of the account. Sophisticated versions of the attack include spoofing the social network’s cell number or short code.
Here is an image of he attack as shared by MaCaw::
One thought on “Attacks Against Verification-Code-to-Cell Two-Factor Authentication”